Details
-
Bug
-
Status: Closed
-
Major
-
Resolution: Fixed
-
None
Description
How to reproduce:
- Create an user A - admin
- Create a user B
- Log in with user B and go to your profile
- Update user B full name to
"><img src=x onerror=prompt(123)>
- Logout
- Login with user A
- MAke sure that user B does not have permission to browse the project you will use
- create a test execution and add a test
- Click on actions -> assign -> search for user B and select it
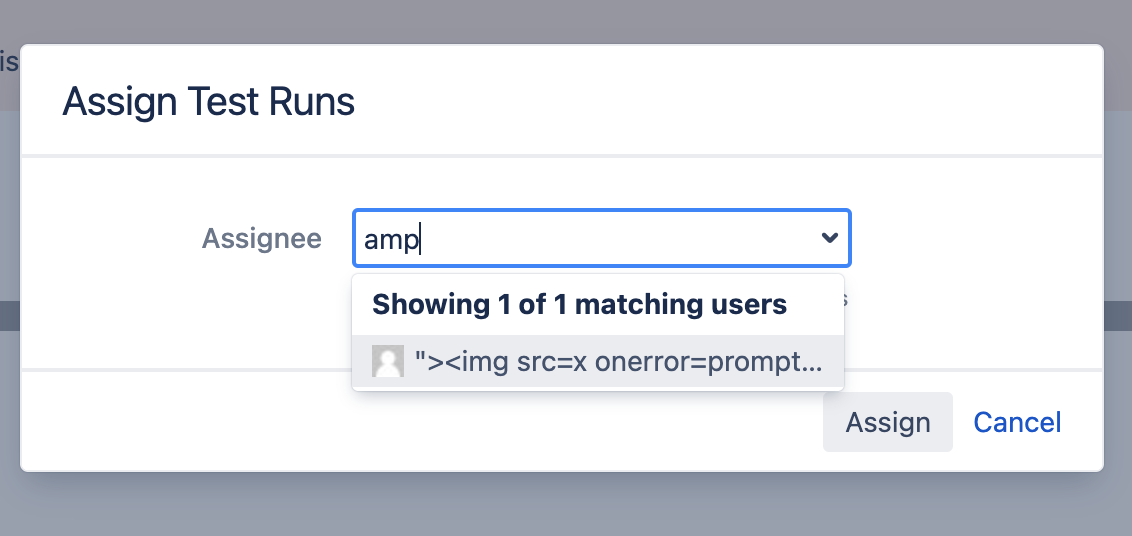
- Click Assign
- The dialog is closed and the prompt appears
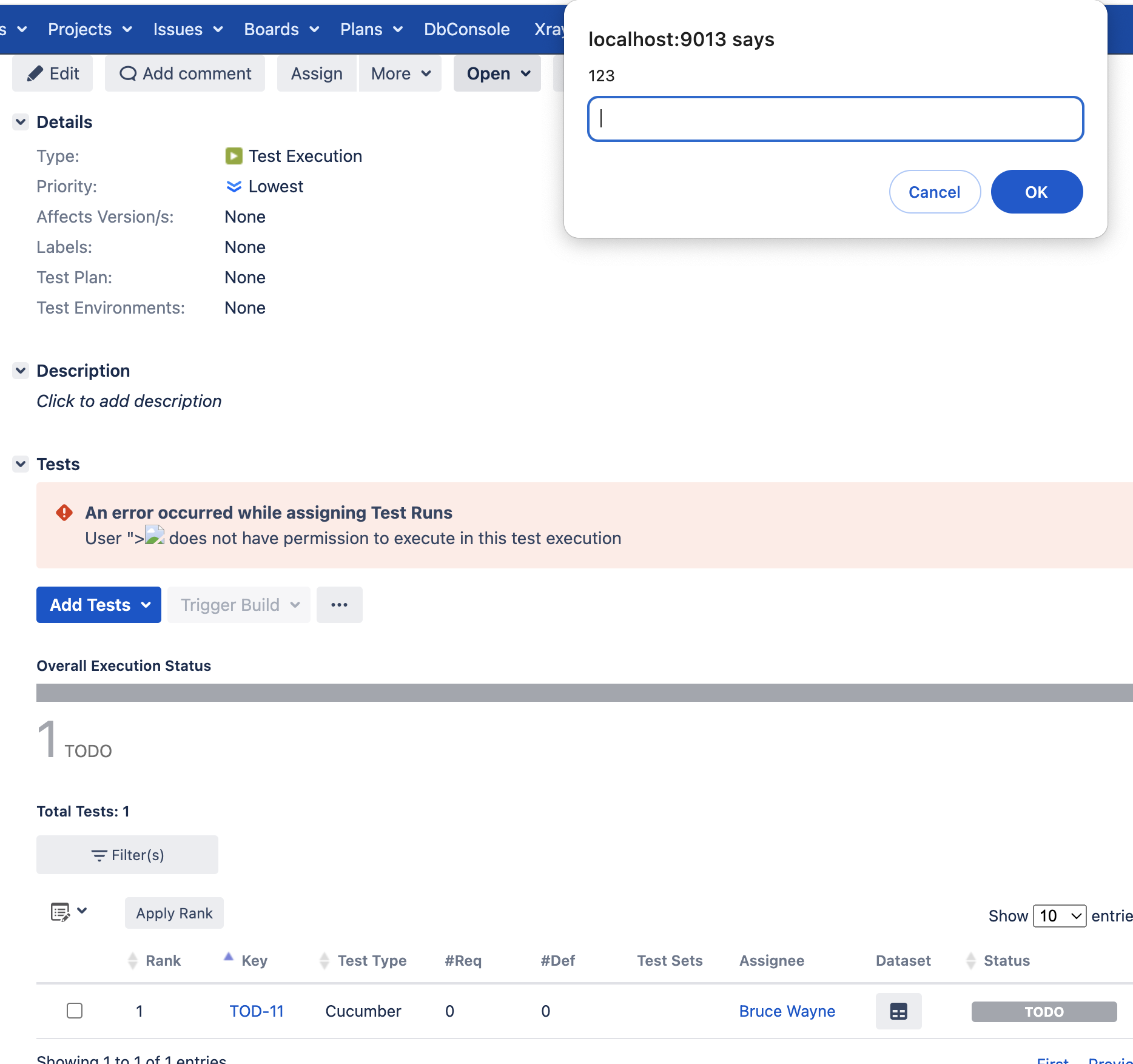
What is this ticket?
This ticket tracks the corresponding Bugcrowd submission 1b8e95f3-0075-492b-8132-77287611532c. Please make a note of the triage and remediation due dates for this ticket.
You are not expected to update the status of the ticket. We will automatically sync the status of the Bugcrowd submission for you :smiley: Please continue to accept, reject, and close submissions directly in the Bugcrowd portal.
What can I do with this ticket?
:one: Ensure that you are actioning on the submission within the Triage Due Date & Remediation Due Date. Learn more about our Bug Fix Policy here.
:two: Request an SLA extension if you need more time. Learn more about SLA management here.
:three: Engage with our Atlassian Security team by simply commenting on the ticket.
:four: Use our partner dashboard to monitor all your SLA’s at one place and analyze trends.
Ticket updates:
If you are interested in receiving notifications on all ticket updates, please add yourself to the watchers list.
Requesting a SLA extension:
If you need to request an extension to fix the vulnerability, transition this ticket to the
EXTENSION REQUESTED
status.
SLA violation notifications:
You will be notified through email and this ticket as the SLA Due dates approach.
:flag_on: If you would like to de-list/retire your marketplace app, please create a request here. After you have created the request, please comment with a link to the ticket. Lastly, transition this ticket to the
ATLASSIAN INPUT REQUESTED
status.
:question_mark: Need any other help? Please comment on this ticket or you can create a ticket here.
- Stored Cross-Site Scripting (Privileged User to Privilege Elevation)
-
- Overview of the Vulnerability
Stored Cross-Site Scripting (XSS) is a type of injection attack where malicious JavaScript is injected into a website. When a user visits the affected web page, the Javascript executes within that user’s browser in the context of this domain. Stored XSS can be found on this domain which allows an attacker to submit data to a form and escalate from a privileged user to a higher privileged user, which could include an Administrator level user.
When an attacker can control code that is executed within a user’s browser, they are able to carry out any actions that the user is able to perform, including accessing any of the user's data and modifying information within the user’s permissions. This can result in modification, deletion, or theft of data, including accessing or deleting files, or stealing session cookies which an attacker could use to hijack a user’s session.
-
- Business Impact
Stored XSS at [Xray](https://marketplace.atlassian.com/apps/1211769/xray-test-management-for-jira?hosting=datacenter&tab=overview) add-on via [User profile name] at assign [Test permission error]
-
- Steps to Reproduce
1. Admin install [Xray](https://marketplace.atlassian.com/apps/1211769/xray-test-management-for-jira?hosting=datacenter&tab=overview) add-on.
1. Admin Add new UserB with user role.
1. UserB navigate to their account and inject XSS Payload in profile name.
> 
1. Admin navigate to {}Project > Create project > select Xray project{}.
> 
1. Admin navigate to {}Xray project > Project setting > Users and roles{} then restrict project for admin only.
> 
1. Navigate to {}Xray project > Project setting > Permissions{} then restrict project for admin only.
> 
1. Admin create `Test Execution and Test issue`
> 
1. Admin navigate to {}Test Execution > then at Test section add Test issue created previously.{}
> 
1. Admin After link test {}click in checkbox > Action > Assign{}
> 
1. If {}Admin/Any other users{} select UserB and click __Assign; Observe the JavaScript payload being executed
> 
> 
-
- Proof of Concept (PoC)
[2024-01-02%2002-53-45.mp4](https://bugcrowd.com/xpandit/submissions/1b8e95f3-0075-492b-8132-77287611532c/attachments/d5418b13-bfc1-49fe-b5f8-75dec34d56e9 "2024-01-02%2002-53-45.mp4")
Bugcrowd Submission Info:
- Proof of Concept (PoC)
Attachments
Issue Links
- links to
